What We Do
Custom-Tailored Services & Solutions
Whatever the threat, JFL’s field-tested experts utilize innovative techniques and technologies to ensure the secure optimization of your operations.
Our Commitment
Security is the Foundation of Success
Working with Federal agencies and thriving companies, JFL prioritizes its clients’ interests by helping to create a safe and secure environment.
Portability & Speed
Our Signature American-Made Products
JFL's Mobile Air Cyber Kit is produced in the USA and is specifically optimized for air travel. This on-the-go network system can accommodate a variety of server-switch-router combinations making it ready for any and all IT operations.
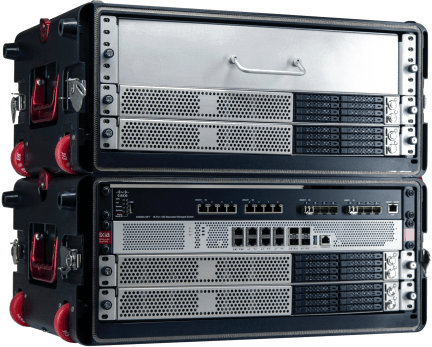
Mobile Air Cyber Kit
This custom military-grade Mobile Air Cyber Kit (MACK) is a top-tier IT network system that can be tailored to client specifications.
- Rugged – electromagnetic pulse (EMP) protected and made of aircraft aluminum
- Versatile – stackable, with room for servers, routers, switches and laptops
- Portable – suitcase-style, TSA-friendly, fits in an overhead bin
- Secure – equipped with high-performance JFL servers & dual lock system
1U and 2U J-Series Enterprise Servers
Field- and office-tested, JFL’s 1000 (1U) and 2000 (2U) J-Series servers are custom-designed for the most demanding IT requirements in the world.
- Unique – custom cooling, power and form factor design
- Portable – up to four fit in each MACK for optimal on-site use
- Rugged – electromagnetic pulse (EMP) protected, military-approved
- High-Performing – fitted with Intel adapters and microprocessors


Our Culture
The Company We Keep
At JFL, people come first. Clients, partners and team members are valued and treated with respect. Together, through collaboration and communication we are able to push the envelope with smart and responsive security solutions.